New Released Braindump2go Microsoft 70-247 Dumps PDF – Questions and Answers Updated with Microsoft Official Exam Center! Visit Braindump2go and download our 70-247 Exam Questions Now, Pass 70-247 100% at your first time!
Vendor: Microsoft
Exam Code: 70-247
Exam Name: Configuring and Deploying a Private Cloud with System Center 2012
QUESTION 181
Hotspot Questions
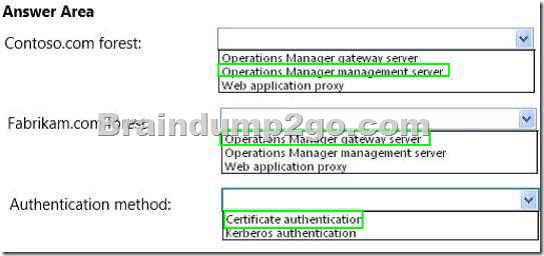
Your network contains an Active Directory forest named contoso.com.
The network of a prospective client contains an Active Directory forest named fabrikam.com.
You need to design the placement of System Center 2012 R2 components to meet the following requirements:
– Ensure that administrators from the contoso.com forest can monitor the computers in both forests.
– Minimize the number of firewall ports open between the organizations.
What should you deploy in each forest and which authentication method should you use? To answer, select the appropriate options in the answer area.

Answer:
QUESTION 182
You have a private cloud infrastructure that uses System Center 2012 R2 Virtual Machine Manager (VMM).
You plan to host several hundred private clouds for different customers by using the infrastructure.
You need to ensure that all of the customers can use any IP address range in their private cloud.
What is the best approach to achieve the goal?
More than one answer choice may achieve the goal. Select the BEST answer.
A. Create a virtual machine network that uses network virtualization.
B. Install a VMM Network Virtualization for Generic Routing Encapsulation (NVGRE) gateway in each
private cloud.
C. Install the IP Address Management (IPAM) Server feature in each private cloud.
D. Create a virtual machine network that uses VLAN network isolation.
Answer: A
Explanation:
Network Virtualization introduced in Windows Server 2012 Hyper-V provides administrators with the ability to create multiple virtual networks on a shared physical network. In this approach to isolation, each tenant gets a complete virtual network, which includes support for virtual subnets and virtual routing. Tenants can even use their own IP addresses and subnets in these virtual networks, even if these conflict with or overlap with those used by other tenants.
Ref: http://blogs.technet.com/b/scvmm/archive/2013/06/17/logical-networks-part-v-network- virtualization.aspx
QUESTION 183
Your company has a private cloud that is managed by a System Center 2012 Virtual Machine Manager (VMM) infrastructure.
The infrastructure contains a server named Server1 that has VMM installed.
You plan to deploy the Hyper-V server role to a server named Server2.
Server2 runs Windows Server 2008 R2. Server2 is member of a workgroup.
You need to add Server2 to the VMM fabric.
What should you do? (Each correct answer presents part of the solution. Choose three.)
A. From the VMM Administrator Console, run the Add Resource Wizard, and then click Windows
Server computers in a perimeter network.
B. From the VMM 2012 installation media, install the VMM agent on Server2.
C. From the VMM Administrator Console, run the Add Resource Wizard, and then click Windows
Server computer in an untrusted Active Directory domain.
D. Copy the SecurityFile.txt file from Server2 to Server1.
E. From the Services console on Server1, start the SSDP Discovery service.
F. Copy the ApplicationHost.config file from Server2 to Server1.
Answer: ABD
QUESTION 184
Your network contains a server named Server1 that has System Center 2012 Virtual Machine Manager (VMM) installed.
You plan to deploy a service named Service1.
Service1 will contain three tiers. Each tier will contain 10 instances.
You need to configure the service template to ensure that when an application in Service1 is upgraded, Service1 remains available.
What should you configure for each tier?
A. The maximum instance count
B. The preferred servicing order
C. The number of upgrade domains
D. The minimum instance count
E. The preferred deployment order
Answer: C
Explanation:
To minimize service interruptions when a tier is updated in-place, you can specify more than one upgrade domain in the tier properties. When the tier is updated, VMM updates the virtual machines in the tier according to the upgrade domain to which they belong. VMM upgrades one upgrade domain at a time, shutting down the virtual machines running within the upgrade domain, updating them, bringing them back online, and then moving on to the next upgrade domain. By shutting down only the virtual machines running within the current upgrade domain, VMM ensures that an upgrade takes place with the least possible impact to the running service.
http://technet.microsoft.com/en-us/library/gg675089.aspx
QUESTION 185
You are creating a Server Application Virtualization (Server App-V) package named Package1 of an application named Appl. Package1 will be included in a System Center 2012 R2 Virtual Machine Manager (VMM) service template.
You need to configure Package1 to ensure that you can modify the settings of App1 from the properties of the service template.
What should you do?
A. From the Server App-V Sequencer, click Add Deployment Configuration Item.
B. Modify the SFT file of Package1.
C. From the Server App-V Sequencer, configure the Properties of the package.
D. Modify the Open Software Description (OSD) file of Package1.
Answer: A
QUESTION 186
You have a deployment of System Center 2012 R2 Virtual Machine Manager (VMM).
You deploy a service by using a service template.
You need to add an additional tier to the service.
The solution must minimize the amount of downtime for the service.
What should you do first from the Virtual Machine Manager console?
A. Create a new version of the service template.
B. Use the Clone option.
C. Create a new service template.
D. Use the Scale Out option.
Answer: A
QUESTION 187
An organization has a private cloud infrastructure. The organization uses Windows Server 2012 R2 servers that have the Hyper-V role installed. The organization uses ail components of System Center 2012 R2.
You use Virtual Machine Manager to configure four clouds and self-service groups.
In addition, you configure price sheets for chargeback reporting in Service Manager.
You must implement chargeback for private cloud customers.
You need to ensure that chargeback reports in Service Manager will return data.
Which three actions should you perform? Each correct answer presents part of the solution.
A. In Service Manager, configure the Virtual Machine Manager Connector.
B. Configure integration between Virtual Machine Manager and Operations Manager.
C. Import a list of Hyper-V host servers into Service Manager by using the Import Instances from
the CSV File tool.
D. In Service Manager, configure the Operations Manager configuration item connector.
E. In Service Manager, configure the Configuration Manager Connector.
F. In Service Manager, configure the Orchestrator connector.
Answer: ABD
Explanation:
http://blogs.technet.com/b/privatecloud/archive/2013/02/19/chargeback-with-system-center-2012-sp1-tutorial.aspx
QUESTION 188
Hotspot Question
A company has a single Active Directory Domain Services (AD DS) domain and Windows Server 2012 R2 servers that have the Hyper-V role installed. The company uses System Center 2012 R2 Virtual Machine Manager (VMM) to manage the Hyper-V environment. Users access company resources from the Internet.
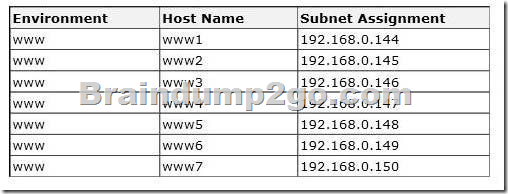
There is an existing front-end web server farm that contains virtual machines (VMs), as shown in the Front-end Web Server Farm exhibit. (Click the Exhibit button.)
You use the VMs to deliver a website to the Internet.

The servers are configured as shown in the following table:
You preform connectivity tests between all of the front-end web servers. The connectivity tests all have the same results, as shown in the Windows PowerShell exhibit. (Click the Exhibit button.)
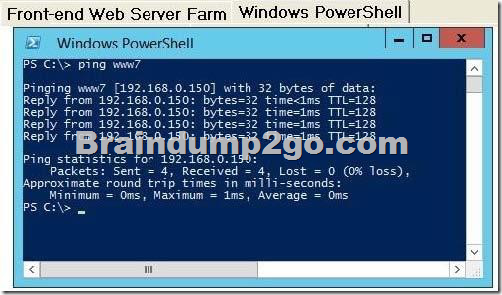
The company plans to enhance overall security of the virtual environment. The front-end web servers must NOT be able to communicate with each other.
You need to implement changes to the environment. For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
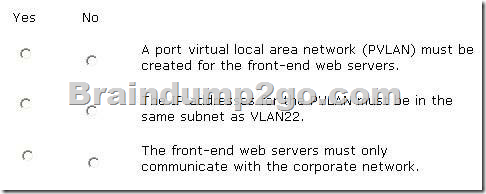
Answer:
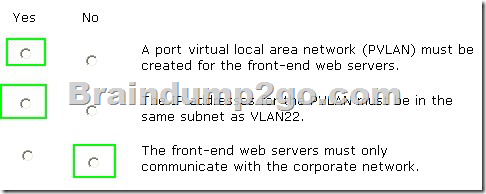
Explanation:
http://blogs.technet.com/b/scvmm/archive/2013/06/04/logical-networks-part-iv-pvlan-isolation.aspx
QUESTION 189
An organization has private and public cloud resources.
The organization has Windows Server 2012 R2 servers that have the Hyper-V role installed.
You have one four-node cluster of Hyper-V host servers.
You use System Center 2012 R2.
The virtual machines that run on the cluster must remain online when you install updates on the Hyper-V host servers.
You need to install updates on the Hyper-V host servers.
What should you do?
A. Configure Windows Serve’ Update Services (WSUS) to provide updates to the Hyper-V host servers
in the cluster.
B. Add all the virtual machines hosted on the cluster to a collection in System Center 2012 R2
Configuration Manager. Deploy updates to the collection.
C. Use the Cluster-Aware Updating (CAU) wizard.
D. Configure Windows Update on the Hyper-V host servers to download updates from Microsoft Update.
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/gg675088.aspx
QUESTION 190
Drag and Drop Question
A company has a single-domain Active Directory Domain Services (AD DS) environment.
Some servers and all domain controllers are deployed on the internal network. All servers in the perimeter network are joined to a workgroup. The company uses System Center 2012 R2 Operations Manager to monitor the server infrastructure on the internal network.
The company plans to use Audit Collection Services (ACS) for one Internet Information Services (IIS) server that is in the perimeter network.
You need to configure the authentication type and ACS role for Operations Manager and the IIS server.
How should you configure the servers? To answer, drag the appropriate authentication type and ACS role to the location or locations in the answer area. Each authentication type and ACS role may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
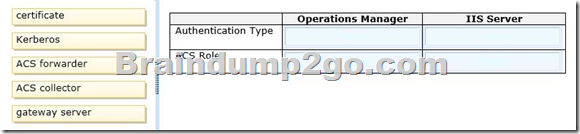
Answer:

Explanation:
http://technet.microsoft.com/en-us/library/hh872886.aspx
Braindump2go New Published Exam Dumps: Microsoft 70-247 Practice Tests Questions, 206 Latest Questions and Answers from Official Exam Centre Guarantee You a 100% Pass! Free Download Instantly!